CSRF In BigTree CMS
Posted on Sun 08 March 2015 in Web Hacking
Yesterday I found a cross site request forgery (CSRF) vulnerability in the latest version of BigTree CMS (at the time of writing version 1.4.5).
This is a little explaination of the vulnerability and how to exploit it.
The Vulnerability
The vulnerability is in the account settings request, which is used to change the account name, company and password.
A normal request looks like this:
1 2 3 4 5 6 7 8 9 10 11 12 13 | |
The vulnerability exists in [BigTreeROOT]/core/admin/modules/users/profile/update.php:
1 2 3 4 5 | |
Here is clearly isn't doing any checks to prevent CSRF.
The Exploit
So exploiting this is very simple, you just have to lure someone who is already logged into the application is visit a page containing this code:
1 2 3 4 5 6 7 8 9 10 11 12 | |
The values here can be changed to anything, it just automatically issues a POST request to http:/bigtree/site/index.php/admin/users/profile/update/ with the following arguments:
name=admin&password=newpassword&company=foobar
Unfortunately it is reasonably intrusive because when loaded the victim will see this:
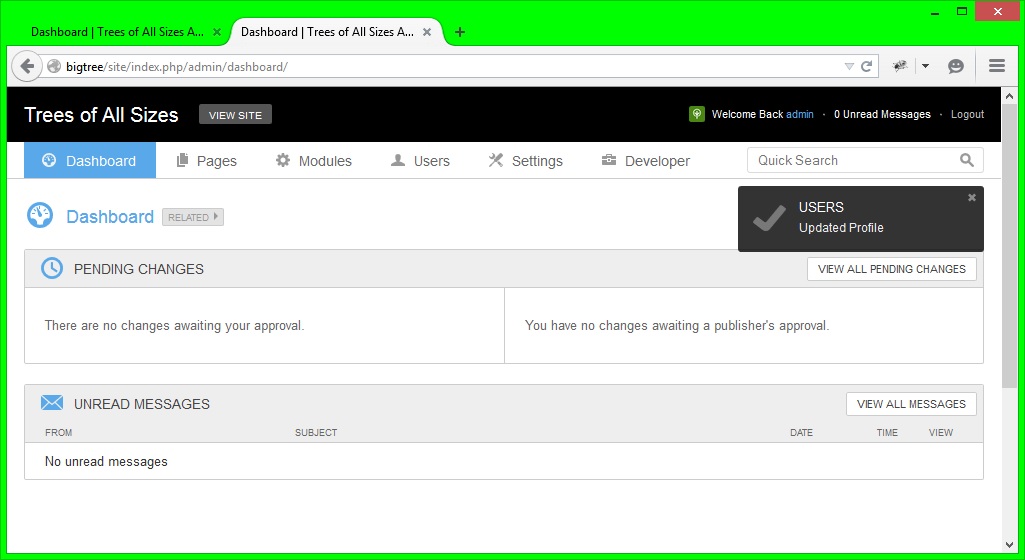
So the user will immediately know that their profile details might have changed.
The Fix
So I contacted Tim Buckingham (the lead developer for BigTree CMS) about this issue yesterday (on 7th March 2015) and he replied the next day informing me that he'd fixed the issue.
You can see the fix here.
The next full releases of BigTree CMS (4.1.6 and 4.0.10) should be out next week and will incorporate this fix.
Happy Hacking :-)
Update (07/04/2015): BigTree CMS have finally released the next version (4.2) that includes the fix, you can download the latest version from here.